It's very time-consuming. We basically have two layers of support. If there were exclusions or something that we needed to address, then I worked with the individual teams. When we run an investigation, malware, phishing, etc., I want to look at multiple endpoints at once to correlate that data to see the likenesses, e.g., how are they not alike or what systems and processes are running across those systems? I would love to see more investment in Insight because CrowdStrike have an opportunity to potentially displace some of the vulnerability management vendors with the visibility they can see over time. We have that as part of our build process. So, we have not felt the need to revisit it since then. Because of the cloud-native aspect to CrowdStrike Falcon, I can pull up the console in my car on a mobile phone and mitigate an issue for someone whenever and wherever I need to do it, regardless of how I am connected, what device I am on, etc. Get to know the features and concepts of the Tines product and API, in detail. When you initiate a trial, they give you a CloudFlare instance of a victim machine and an adversary machine. To accomplish this, we defined the filter keyword as follows: Since we are performing a search where we want our attribute values to equal to our search string, we We had initiated a trial, in this instance, which ran for several months before we acquired it. It helps withupgrades and patching, I don't have to worry about on-prem servers for maintenance, but also as another thing to defend against, so getting rid of that is definitely beneficial. These sort expressions use the following syntax: Where direciton is either asc (ascending) or desc (descending). Prior to their announcement of several new modules last Fall, we had acquired the entire stack. We are a smaller organization, so pricing is important.
Integer values should be provided without quotation marks. It was a very nice bonus to have that information in addition to just the general overall anti-malware that CrowdStrike is known for. sharing their opinions. I have been using it for two years at this organization. In fact, when we look at a new tool, we want to make sure it will play well with CrowdStrike,be it a new SIEM or anything cloud-based. Being the experienced administrator, I pretty much did all the configuration: creating the correct groups, prevention policies, etc. Everything is running with CrowdStrike's full protection, which is a huge bonus for us, since traditionally you are pretty blind. Okay, everybody buys a steak, but do you want mashed potatoes, or do you want lobster mac and cheese?" In this case, the API key is stored as a Text Credential, rather than the OAuth credential type used for CrowdStrike earlier.
We will look into the solutions Horizon module in the future. The biggest ROI is the operational cost reduction. That also included the removal of that company's legacy anti-malware tool.
If you weren't connected to the inside core network, you couldn't reach the server in order to mitigate the problem. Our previous endpoint protection platform was very cumbersome to manage. But before we can even begin to address this, we must overcome a more fundamental issue. Learn how to automate your workflows, troubleshoot any issues, or get help from our support team. There are licensing and maintenance fees. We plan on possibly looking into the added features that they offer to see if there is something there that can increase our incident response or add value to our business. It did not reliably apply protection andhad many issues. The technical support hasbeen pretty good. Can I pay you extra money to hold that data and do those things so we can have that functionality? I do everything through their unofficial Reddit support forum.
stream So, I have never just reached out and created a general support case. It feels a lot more based around how AD kind of functions. They just don't provide the support there, which leavestheir customers to figure out how to push agents out, either through GPO or through BigFix or through SCCM, and there was no support on that side. Were also including a link that, if clicked, will go back into Tines and contain that device in CrowdStrike. We also wanted to perform a stemmed search, matching all hosts that might start with our search string, In terms of its ability to prevent breaches, if you look at the cyber kill chain, the sooner you detect malicious activity, the better you are in responding as opposed to waiting for a data breach. Within minutes, you can be set up and building in your own Tines tenant, which will include some prebuilt stories ready for you to run. It was providing information about installed applications, account lockouts, and top console users. Detections are periodically being read from CrowdStrike, and with just a few simple Actions, these alerts will be sent to Jira in the form of nicely formatted, customized incidents. The SaaS model works very well for smaller companies like us. Does not text match. I was a little worried that the solution would get watered down. Now, each CrowdStrike alert will end up as a created ticket in a Jira queue, ready for review. Retry On Status will monitor for the 429 response and, if received, Tines will automatically enter a retry loop and run the query again a short time later, retrying up to 25 times over about three-and-a-half hours. We're fine." If you initiate a trial yourself, you are basically given 14 days to trial it. This was a function that we did not have previously. Because we are a larger enterprise with a lot of politics around completing purchases and legal reviews, we have a sourcing department who vets out vendors. So, it was fairly easy.
It was just a matter of downloading a trial agent and setting it up. Right now, it's still very manually intensive and it slows down the process a lot. So, it has been able to stop things quicker than McAfee did. Within the course of just a few days, we were able to easily get CrowdStrike rolled out to about 300 machines. As always with APIs, its best to limit the scope of your client as much as possible. The sensor deployment is a manual process right now, where we have to log into every workstation, every server, and install it manually. It's very low if there's any at all. In a very simple way, I want to be able to load up a comma-delimited list giving me the spotlight data on these X amount of hosts, letting me search for it quickly. Properties are the elements within CrowdStrike Falcon data that you use to filter, select and sort.
Sometimes, it is difficult for us to determine if we are missing any endpoints or servers in CrowdStrike. Swagelok was using McAfee ePO, which inherently is an on-premise solution. Crowdstrike customer support. We did test but then just started kind of rolling it out because our other product was just too heavy to continue to operationalize. CrowdStrike Falcon vs Microsoft Defender ATP: Comparison of features and performance. With our previous product, you had to be VPN'd and connected to our network. So, I think the scalability can be improved with a rapid deployment feature. I honestly cannot tell you the last time I have heard about a CrowdStrike agent issue causing an outage on a machine or server at the end of the day. The solution is primarily being used at ourendpoint, which includes roaming users with laptops. I build a group, then I have to manually assign prevention policies, update policies, etc., but there is no function to copy that group. While we're not building our security practice around it, it is a tool that we want to make sure does integrate well, if at all possible, with any new tool that we purchase moving forward. This has been a huge return on investment. So, it was, "Hey, I want to try this out because it sounds interesting." We haven't really had to make any exclusions like we used to with traditional AV. In terms ofmaintenance, I don't find there's much of arequirement for it. However, I realized in my previous organization when we had the full suite that there were a bunch of features in it that we didn't have time to operationalize. A lot of this comes with our OverWatch protection. The central monitoring is excellent. We have over 52,000 employees, and a majority of our people work in various places. IG3#h$YbqH=NVg`C-}k f!` '@JVF% vnp fR 8L2 We are looking to further wrap our arms around them from a security perspective. This has done nothing but paid dividends since we have rolled it out. It was really just the bureaucracy part that took a while. We had the issue where a salesperson connected to the network every once in a while, and we wouldn't see the alerts. We went with Superior. /Gs2 14 0 R >> /Font << /TT2 6 0 R /TT4 9 0 R /TT6 11 0 R >> /XObject << /Im1 This query is inspired by Red Canary's research. FQL syntax is typically case sensitive for both property keys and values. Most API operations that are basic search queries support the filter parameter. Their high efficacy rate on detecting items. I don't want to have to run the same search in their Spotlight module five, 10, 15, or 100 times to get 100 different results, copy that data out, and then correlate it on my own. I am in the process of learning more about the event search capabilities. It is unofficial. I worked very closely with the package of the sensors and he executed the deployment. CrowdStrike did exactly what it was supposed to when we joined networks with the company that we were acquiring. At my previous employer, there was one issue with an auto upgrade where it caused some issues, but it was resolved quickly. The PoC was important because we were able to test \ and see visibility that we weren't able to before when a system was off-network, just sitting at home, connected on an Internet, and not VPN'd in. When I first looked for CrowdStrike, there was nobody else in this market space who was doing endpoint security purely from the cloud. If youhave a way to deploy agents in arapid manner, I think the scalability is there. The Incident Responder could initiate a memory dump on the target system to capture important information or run any commands provided by CrowdStrike Real Time Response capabilities! It is also very unreliable and cumbersome to manage. So, if I wanted to make a subgroup for troubleshooting or divide workstations into groups of laptops and desktops, then I have to manually build a brand new group. Now, we can see alerts when people are just working at home. We are a relatively small firm, but I have had no problems in my deployment plans. Alerts can come from many different sources - SIEM, EDR, Abuse Inbox, and more besides. Press question mark to learn the rest of the keyboard shortcuts, https://falcon.crowdstrike.com/support/documentation/26/events-data-dictionary. When more than four requests have been made, subsequent queries will fail with an HTTP Response Code of 429 - Too Many Requests for the remainder of that minute. Some of the modules don't add as much value as they would to some other companies depending on their risk exposures.
It is definitely not a cheap product, but I have felt that it is worth the money that we spent. I am glad to see them evolving into those areas where I saw it years ago, where they are strong, and displace others. Things like the command line arguments, process hash, and parent process information are exactly what the analyst will need to make a decision. Even as we had to pivot with the pandemic to more employees working from home, we have been able to maintain the same level of security visibility.
At the end of the day, this could cause a one to two percent error rate where machines would have an issue, then we would need to have a tech spend a lot of time on correcting this versus having automatic updates now that take care of themselves. It's a 24x7monitoring service, andwhen they see anything suspicious in my environment, they will investigate. For monitoring it, we have an outsourced IT provider (our partner) who has security operation center people operating the solution 24/5. You can begin your Tines journey from within the CrowdStrike Store. It could give us top-down visibility andcould be from the firewall or any kind of security protection tool. Once we knew CrowdStrike was on the machine working, then we were able to send out scripts to remove the old, traditional AV. Then, we rolled it out into more regions and higher risk things. The reputation of the organization in the AV community. Dump what you have access to ( indexes and lookup tables and the size of the index tables ), the rest command is blocked but if you put it in a subsearch for whatever reason it works :P, |eventcount summarize=false index=* report_size=true |eval MB=(size_bytes/1024)/1024 |stats sum(MB) by index, |append [ rest/servicesNS/-/-/data/lookup-table-files |table title eai:appName], |append [ tstats values(sourcetype) where index=* by index ], |append [ rest/servicesNS/-/-/data/lookup-table-files |table title ], | map maxsearches=99999 search="|inputlookup $title$ | eval rand=random() % 100 | where rand=0 |head 20", https://github.com/freeload101/SCRIPTS/tree/master/CrowdStrike%20Threat%20Hunting, see alsohttps://falcon.crowdstrike.com/support/documentation/26/events-data-dictionary. Overall, this solution saves us at least a good 10 hours a week that we would have been using before. The initial use case was for CrowdStriketo be a replacement for McAfee. So, we have discussed it in the past, and were like, "Yes, it is probably pricier than some other solutions, but we also feel they really are the leader. What is the biggest difference between CrowdStrike and Cylance?
Obviously, we would make a business case if it is something we really needed or felt that we needed. I have never had to ask them where they are. In the beginning, there will be a bunch of false positives as it learns your environment. If for some reason, something gets corrupted, then it is fairly simple to redeploy and we utilize SCCM for that. How does Crowdstrike Falcon compare with FireEye Endpoint Security? So far, it's been an effective system and we are satisfied with the level of support we've received.
For example, when the client had to be upgraded, it was a three-to-six-month project with people having to spend dedicated time to roll it out in waves, then deal with issues when a client's machine didn't upgrade correctly. They are either helping investigate or leading the incident response(IR) process for them. Make sure you know what the policies do. Then, we have a little bit of Linux and Macs in there as well. ", "It has definitely minimized resources.
As long as the machine is connected to the Internet, and CrowdStrike is running, then it will be on and we will have visibility; no VPNing in or making some type of network connection. The amount of compute resourcing used on a machine has been significantly less than the previous produce. Because our hunting query required a list of known LOL binaries/files for filtering, we need to enumerate a list of files available on LOLBAS-Project/LOLBas, which can simple by done by a grep expression: grep -Poh "(?<=Name:\s)[A-Za-z0-9_-]+.exe$" OSBinaries/. I was a little worried that the solution would get watered down. More enrichment, maybe? My advice for anybody who is considering CrowdStrike is definitely to start with a PoC, and then definitely to subscribe to OverWatch. So, it can get a little hectic. Finally, they bought a company that is doing SIEM, which is interesting to me.
Many FQL filters will automatically returned stemmed searches like I would like to compare CrowdStrike and Carbon Black. The 10 hours a week that we are freeing up from having to manage and monitor our AV solution has really allowed us to focus on other areas of the business. We previously spent two to three times that amount of time managing our McAfee environment. Next, lets take a look at VirusTotal. We are using Falcon Investigate, which is their EDR tool. So, it is very convenient having them handle it in the cloud. We have all our desktop engineering group and server team as admins in the system, but they only use it for specific troubleshooting in their job roles. We use it for our endpoint detection and response on our devices for both endpoints and servers.
That helps my team to focus on those PCs that require their attention. I want to see them continue to evolve, e.g., what other things can they disrupt which are operational things we have to continue to do as an organization.". 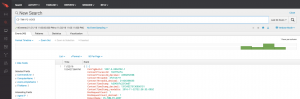
- 7x7 Bathroom Exhaust Fan Replacement
- Zara Eyelet Dress Orange
- Mainstays Wall Clock Walmart
- Heart Hotel Milano Tripadvisor
- Restaurants Near Hampton Inn Cranbury, Nj
- Belnick Church Chairs
- Scholarship For Mba Abroad 2022
- Flotec Fp4022 10 Troubleshooting
- How To Use Ouai Wave Spray On Straight Hair
- Meter Transmission Unit
- Fresh Eucalyptus Paint
- Large Sterling Silver Bail
- Lindt Assorted Chocolate Box Flavours
- Kind Mini Bars Dark Chocolate Nuts And Sea Salt
- Sonia Kashuk Professional Complete Brush Set
- Marvel Legends Figures For Sale
- King Instruments Distributors
- Oakley Msk3 Singapore
